Administrative Roles Explained#
User Accounts created on the Directory Server can be granted some rights (Permissions) to become an Administrative account, so they can manage the permissions assigned to other accounts, the settings of a domain, or a combination of them.
Carbonio employs a hierarchical role-based access control system, offering six predefined administrative roles. Each role inherits the permissions of the roles beneath it, allowing for flexible and granular delegation of administrative responsibilities.
1 - Global Administrator
└── 2 - Domain Administrator
└── 3 - Delegated Domain Administrator
└── 4 - User Management Domain Administrator
├── 5 - Group Management Domain Administrator
└── 6 - Help Desk Domain Administrator
In this page we describe the main pre-built roles (Global Administrators, Domain Administrators, Delegated (Domain) Administrators, User Management (Domain) Administrators, Group Management (Domain) Administrator, Help Desk (Domain) Administrators) and their associated permissions. Users that belong to these groups automatically inherit the permissions of the group. Pre-built roles are hierarchical, meaning that every role has some peculiar permission plus all the permissions of the roles below: for example, a Delegated Domain Admin also possesses all permissions of User, Group, and Help Desk Administrators.
Except for the Global Administrators, who has access to all domains and setting defined in the Carbonio Admin Panel, all other pre-built roles allow to manage the settings of one domain or a subset of a domain.
To facilitate the presentation of the information of each Administrator, we organise them as follows:
On which parts of the Carbonio infrastructure the Admin can operate.
A summary of the permissions granted to the Administrator
What the Administrator can not do, compared to the type of Administrator that is immediately above in the hierarchy.
Detailed list of permissions
The full list of permissions granted to the administrator.
Note
The list is initially collapsed, click it to expand it.
Additionally, comparison tables show differences in the permissions of Administrator types.
Infrastructure Settings#
The concept of infrastructure settings is central within Carbonio and typically refers to system-wide or service-level configurations that go beyond the scope of a single domain. Here are some examples of infrastructure settings:
Infrastructure Setting Type |
Examples |
|---|---|
Server/Service Configuration |
Mailstore assignment, LDAP settings, server roles |
Global COS (Class of Service) definitions |
Creating/editing COS that apply across domains |
Resource Allocation |
Quota limits, backup policies, system resource usage |
Security Policies |
Global password policies, two-factor auth configuration |
Monitoring & Analytics |
System-wide reports and logs |
Themes & Branding (Global) |
Login page customization, global UI elements |
Requirements#
These requirements must be satisfied before being able to manage permissions.
-
To be able to use permission, a domain must be first initialised from .
Alternatively, you can initialise a domain from the CLI:
zextras$ carbonio admin initDomainForDelegation example.comReplace example.com with the domain to initialise.
User eligible to become Administrators must have the attribute
zimbraIsDelegationAdminAccountset to True
If during the initialisation you see a red pop up in the Carbonio Admin Panel or the following error message if you issue the command from the CLI:
Admin Auth Token is missing or empty
You can fix this problem by deploying again the CA, issuing the
following command as the zextras user
zextras$ zmcertmgr deployca
Then, initialise again the domain
zextras$ carbonio admin initDomainForDelegation example.com
Note
you can also check whether in the log file
opt/zextras/mailbox.log you find the message:
ERROR [ZxLink Handler Thread] [] extensions -
javax.net.ssl.SSLHandshakeException: PKIX path building failed:
sun.security.provider.certpath.SunCertPathBuilderException:
unable to find valid certification path to requested target
How to Create an Administrator#
To create Administrators, the procedure is slightly different between Global Admins and administrators.
To set an account as a Global Administrator, go to , select the account to promote, and on the Administration tab click the Global Administration switch.
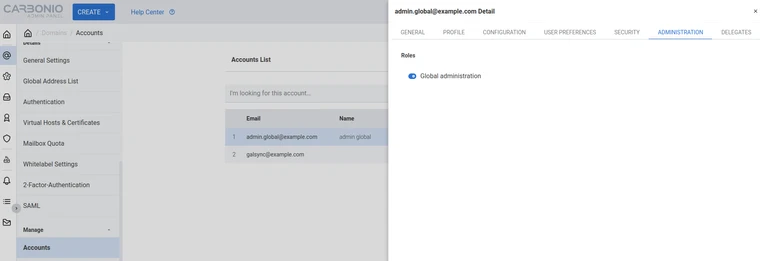
Fig. 19 Adding a Global Administrator.#
To grant an account any other Administrator roles, go to , select the account to promote, and on the Administration tab click the Delegated Administration switch, then select the corresponding permission:
Role |
Permission |
|---|---|
Domain Admin |
|
Delegated Admin |
|
User Management Admin |
|
Group Admin |
|
Help Desk Admin |
|
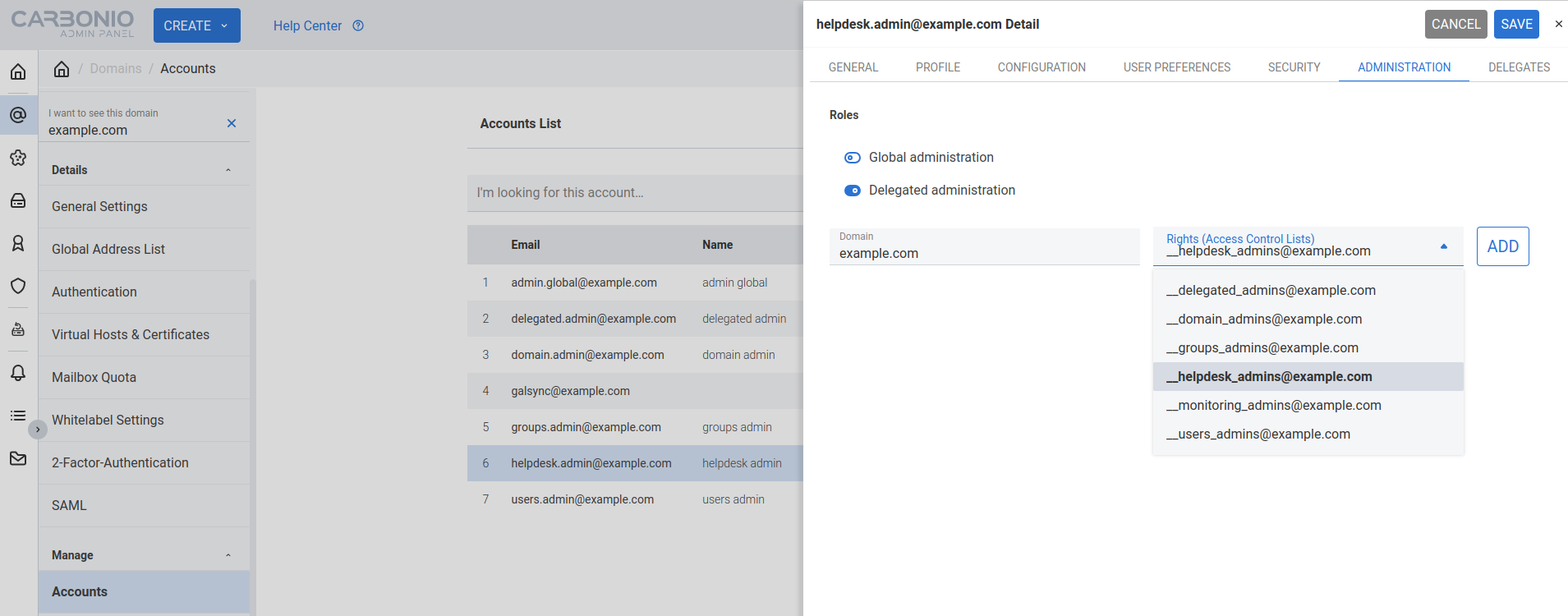
Global Administrators#
Also called Infrastrucure Administrators, they have access to all features in the Carbonio Admin Panel and API, and can manage every aspect of the Carbonio Infrastructure.
Warning
At least one user in your infrastructure needs to be a Global Administrator, but we recommend having at least two.
Entire infrastructure.
Full access to all domains, settings, and configurations.
Manage users, domains, servers, and global settings.
None
Detailed list of Permissions
This is a list of permission that are reserved to the Global administrator only. These are related to the Carbonio infrastructure in its whole.
|
|
Domain Administrators#
The Domain Administrators have a broad control, but strictly limited to one domain and the lifecycle of the objects within the domain. They have no access to Infrastructure Settings.
A specific domain
Manage domain attributes (excluding Assigned Class Of Service, Max Account Number, and Quota)
Control domain themes, GALSync users, authentication settings, virtual hosts, and certificates
Create, modify, and delete other domain administrators
Assign permissions to other domain administrators
Manage analytics at COS and account levels.
They can not modify Assigned Class Of Service, Max Account Number, and Quota
Detailed list of permissions
|
|
Feature / Permission |
Global Administrator |
Domain Administrator |
|---|---|---|
Scope |
Entire Carbonio infrastructure |
Single domain |
Can manage multiple domains |
Yes |
No |
Access to global settings (infrastructure, COS, services, etc.) |
Yes |
No |
Manage users within assigned domain |
Yes |
Yes (for all domains) |
Create/edit/delete other domain admins |
Yes (within the domain) |
Yes (for all domains) |
Assign rights and roles |
Yes (within the domain) |
Yes (Full rights and role delegation) |
Manage themes, GALSync, authentication |
Yes (domain-specific) |
Yes (globally and domain-specific) |
Manage COS (Class of Service) |
Yes |
No |
Modify Assigned COS, Max Account Number, Quota |
Yes |
No |
Access server/infrastructure settings |
Yes |
No |
View analytics |
Yes (for domain/COS/account level) |
Yes (Full analytics access) |
Manage Chats user search across domains |
Yes |
No |
Delegated (Domain) Administrators#
The Delegated (Domain) Administrators are limited to account-level and basic domain settings . They can not assign or change admin roles or modify domain parameters such as virtual hosts, authentication methods or themes but they can manage distribution lists.
Specific domain
Full access to domain settings (excluding infrastructure settings)
View domain attributes
Cannot access infrastructure settings.
Detailed list of permissions
In detail, these are the permissions of a Delegated Administrator.
|
|
Feature / Permission |
Delegated Domain Administrator |
Domain Administrator |
|---|---|---|
Scope |
Single domain |
Single domain |
Manage domain settings (general) |
Yes |
Yes |
Manage infrastructure settings (COS, quota, etc.) |
No |
No (restricted to Global Administrators) |
View domain attributes |
Yes |
Yes |
Create/edit/delete user accounts |
Yes |
Yes |
Assign or change admin roles |
No |
Yes (within a domain) |
Manage GALSync, virtual hosts, certificates |
No |
Yes |
Manage authentication methods |
No |
Yes |
Manage domain themes |
No |
Yes |
Login as managed users |
Yes |
Yes |
View analytics (domain-level) |
No |
Yes |
Modify or view infrastructure settings |
No |
No |
User Management (Domain) Administrators#
User Management Administrators are focused purely on user account operations and have control on lifecycle of the users in the domain. They are suited for HR or Help Desk teams managing users.
User accounts within a domain.
View domain attributes
Create, modify, and delete user accounts (excluding mailstore assignments)
Manage OTPs, aliases, password policies, and account restorations
Login as other users they manage
Can not assign accounts to a specific mailstores.
Detailed list of permissions
These permissions are reserved to a User Management Administrator.
|
|
Feature / Permission |
User Management Administrator |
Delegated Administrator |
|---|---|---|
Scope |
User accounts within a domain |
Full domain-level (excluding infrastructure) |
Create/edit/delete user accounts |
Yes |
Yes |
Assign mailstores to accounts |
No |
No |
Login as users |
Yes |
Yes |
Reset passwords, OTPs, aliases, Auth (mobile/apps) credentials |
Yes |
Yes |
Manage account restoration and undelete |
Yes |
Yes |
Manage distribution lists |
No |
Yes |
Manage GALSync, virtual hosts, certificates |
No |
No |
Manage domain settings |
No |
Yes |
Assign or manage other admins |
No |
No |
View domain attributes |
Yes |
Yes |
Access analytics |
No |
No |
Group Management (Domain) Administrator#
A Group Management Administrator has control on lifecycle of a domain’s distribution lists and their aliases and is an ideal choice for managing group email structures.
Distribution lists within a domain.
View domain attributes
Create, modify, and delete distribution lists (excluding dynamic lists)
Manage distribution list aliases
Cannot manage dynamic distribution lists.
Detailed list of permissions
These permissions are reserved to a Group Management Administrator.
|
|
Feature / Permission |
Group Management Administrator |
User Management Administrator |
|---|---|---|
Scope |
Distribution lists within a domain |
User accounts within a domain |
Create/edit/delete distribution lists |
Yes |
No |
Manage dynamic distribution lists |
No |
No |
Manage distribution list aliases |
Yes |
No |
Create/edit/delete user accounts |
No |
Yes (excluding mailstore assignment) |
Login as users |
No |
Yes |
Reset passwords, OTPs, Auth (mobile/apps) credentials |
No |
Yes |
Restore accounts or undelete data |
No |
Yes |
View domain attributes |
Yes |
Yes |
Manage OTP, password policies |
No |
Yes |
Assign roles or manage other admins |
No |
No |
Access analytics |
No |
No |
Help Desk (Domain) Administrators#
Help Desk (Domain) Administrators can reset passwords within the domain, including all users but administrators, and manage some user information, both in the Carbonio Admin Panel and via API. An Help Desk Administrator is suited for user-level support.
User support within a domain.
View domain attributes
Modify user information (personal data, preferences)
Reset and assign user passwords, application credentials, and OTP codes
Undelete emails, calendars, and contacts
Cannot reset passwords for other administrators.
Detailed list of permissions
These permissions are reserved to a Help Desk Administrator.
|
|
Feature / Permission |
Help Desk Administrator |
Group Management Administrator |
|---|---|---|
Scope |
User support within a domain |
Distribution lists within a domain |
View domain attributes |
Yes |
Yes |
Modify user personal info and preferences |
Yes |
No |
Reset passwords, OTPs, and Auth (mobile/apps) credentials |
Yes |
No |
Suspend/reset HTTP, IMAP sessions |
Yes |
No |
Restore deleted emails, calendars, contacts |
Yes |
No |
Create/edit/delete user accounts |
No |
No |
Create/edit/delete distribution lists |
No |
Yes |
Manage distribution list aliases |
No |
Yes |
Manage dynamic distribution lists |
No |
No |
Assign roles or manage admins |
No |
No |
Access analytics |
No |
No |